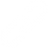By exploiting weaknesses in both the Android and iOS systems, intelligence services and criminal organisations in various countries with dubious attitudes towards democracy have been able to plant the Pegasus spy program in phones of unsuspecting people. The application can spy on anything that happens on the phone. Everything is handed over to the ones who are in control of Pegasus.
In July 2021, it was revealed that the program had been used to spy on those in power, religious profiles, opposition figures and activists. The review revealed that 180 journalists from 20 different countries have been subjected to surveillance, including executives and reporters at CNN, the New York Times and Le Monde. Mexican drug cartels use Pegasus to spy on lawyers, journalists, human rights activists, opposition politicians, anti-corruption lawyers and international commissions of inquiry. Among the more prominent people spied on are the French President Macron and Jeff Bezos, head of Amazon.
The intention of said espionage is, of course, to find compromising facts about obnoxious journalists, oppositionists, human rights defenders and more, so that they can later be prosecuted and eliminated. Or, why behave legally, when just “eliminated” might be good enough?

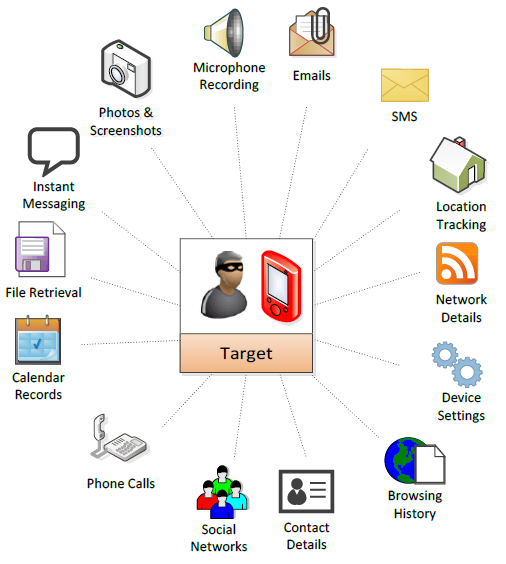
Overall figures on how Pegasus is used in the world, reported by the University of Toronto’s Citizen Lab. The image is available under Creative Commons.

Pegasus was created by the Israeli company NSO Group, probably as early as 2013, with the intention of being used against terrorists. NSO claims that they carefully check who buys the software, so that undemocratic, corrupt states would not get it. Well, the undemocratic, corrupt ones got it anyway and it is now used in, among others, Africa, India, Hungary, Morocco, Turkey, the Middle East, Mexico and in various former Soviet states.
The ones who acquired Pegasus from NSO and spread it on the Internet are called “operators” and in a survey conducted by four researchers at the University of Toronto’s Citizen Lab in 2018, there were 36 operators who snooped on 45 countries. In Mexico alone, there are three operators. See the Read More section.
Everything that Pegasus can steal, according to the University of Toronto’s Citizen Lab. The image is available under Creative Commons.
As Pegasus steals everything, both ongoing calls, video and GPS position, as well as contacts, stored files, photos, web history, conversations, texts, etc., even those you communicate with, will be revealed. Taken together, this makes Pegasus a terrible weapon against dissidents and journalists and their colleagues around the world.
1 No Reason to Give Up
The threat seems to be all-encompassing. Everyone is threatened by espionage nowadays. Why should one even try to fight back?
Of course you should. It is possible to protect yourself against new attacks if you only take basic measures and uphold proper IT sanitation.
Pegasus does not differ all that much from previous spy apps.
2 Zero-Click Attacks
Pegasus is “zero-click” and can infect through sensitive apps without the user doing anything. Sensitive apps include Photos, Apple Music and iMessage.
How does it happen? Many apps found in the various app stores are either created to be Trojan horses directly, or have such poor protection (backdoors) that they act as revolving doors for cybercriminals. There are also an incredible amount of lookalike-apps that look almost the same as the most popular ones, but are malicious. For example, there are hundreds of weather forecasting apps, many of which are malicious from the outset and disclose your user information to the manufacturer, who then sells it to the highest bidder.
According to media, it may seem as if only Apple phones are infected, but Android phones are just as vulnerable.
What should you do to reduce the threat?
- Reduce the attack area. Minimise the amount of apps on the phone. Erase the ones you rarely use.
- Update operating systems and apps regularly, as updates are intended to close security holes.
- But if you are infected, it is not enough to just update the operating system. It does not make the Trojan disappear.
- Protect your work phone by having it unreachable and switched off when not in use.
3 How to Find Out if you are Infected
The problem is that it is difficult to know if you are infected, because Pegasus is good at hiding. Otherwise, it wouldn’t be much of a spyware. Journalists accustomed to the methods of dictatorships, however, mean that after a while they instinctively feel that they are being intercepted, as they are repeatedly contacted by the security services and the police with strange accusations. They change their phones often.
- If you suspect something, you should have a forensic examination of the phone carried out, for example by Reporters without Borders or Amnesty International. In this case, do not factory reset.
-
A database of more than 50,000 telephone numbers of infected people’s telephones has been revealed by Forbidden Stories and Amnesty International, which they have shared with 17 different news organisations. A search page can be found in the Read More section.
- A technologically advanced person may investigate where the phone is secretly sending data, by connecting the phone to one’s own wireless network and examining the data traffic in the router. First, turn off all background apps, such as weather reports, health reports, Spotify (a concealed file sharer), games, and more. Of course, the phone will send data to the person you are communicating with and probably to the manufacturer too, but you will probably also see traffic to advertisers and all sorts of unknown addresses. Make a phone call and see if the unknown traffic increases. Send an email and see if it goes to anyone other than your email manager. It will probably be a chilling experience. Unknown IP addresses can be traced at https://whois.domaintools.com/. Unfortunately, there are thousands of addresses for Pegasus Command & Control servers and they are constantly changing. Also note that decoy pages are common, which, if you look at them, look like ordinary, harmless web pages designed to make you believe that nothing dangerous has happened.
- Please note that whois.net is something completely different!
-
So, what’s Important?
The risky zone, as mapped by the University of Toronto’s Citizen Lab. The image is available under Creative Commons. If you are at risk of being of interest to a country’s security service, it’s time to start watching what you do with the phone.
Well, this will soon apply to anyone who surfs the Internet, who does not want to spread their personal data around or disclose too much to advertising companies.
- Do not click on everything that flashes on the Internet.
- Links can be tricky and hide jumps to malicious sites. If you are going to a site you trust, type the address by hand, do not click on a link. Avoid sites you do not trust.
- If the link seems to be an abbreviated variant (common on social media), do not accept it.
- If you know that the site you are going to, uses https://, you must type it at the beginning of the URL, otherwise the browser could be redirected to an unprotected scam site.
- Bookmark your known, secure sites and use those bookmarks, not links.
- Ignore texts and other messages requesting you to click on links. If the request comes from someone you know, call them before you click, and verify that their account has not been hacked.
- Ignore messages from people you are not well acquainted with on Instagram, Telegram, Tiktok, Facebook and other social media.
- Delete spam and emails from strangers. Do not click on links.
- Do not let anyone else use your phone.
- Save passwords, but delete cookies. Often! https://www.hidden24.co.uk/cookies-and-how-to-get-rid-of-them/
- Just because your friends think an app seems fun or useful, you should not download it: https://www.hidden24.co.uk/apps-that-leak/
- Follow general advice for the safe use of mobile phones.
-
Especially for Those who are Politically Exposed: Two Phones
Use two phones.
Have one for serious jobs, on which you do not do general surfing. Factory reset the phone before you start using it. Feel free to use a non-standard browser that is less likely to become infected. Keep your phone up to date with the latest software updates. Switch off the phone when not in use.
- If you suspect infection, hand over the phone for forensic examination to, for example, Reporters without Borders. In such case, do not factory reset it!
-

Image: Eirik Solheim, Unsplash If your situation is very sensitive, you should change your phone often. How about an old phone that can’t run apps? One that can not connect to the Internet? They still exist. Surf the Internet on a computer instead. Make your notes in a paper notebook.
Sure, this is harder, but you should regard it as if you’re more or less at war. A signal reconnaissance war that could turn into something more serious.
- If you have higher security requirements, like if you work for the government or a municipality, consider an encrypted telephone, which uses secure zones: https://www.hidden24.co.uk/what-is-a-secure-mobile-phone/
-
You can use the other phone to surf as usual, and open unknown links, but remember that if it gets infected, it can be used to spy on you. Switch off the phone when not in use.
Do not surf the Internet in cafes, train stations and the like, because you may be redirected to a malicious site. Just how easily that might happen, you can read here: https://www.hidden24.co.uk/snooping-on-wifi-is-easier-than-you-think/
Hidden24 Recommends
Regard this article as a recommendation from Hidden24. A VPN tunnel does not help your phone in this case, because it is not internet espionage. The tunnel only serves to give Pegasus an encrypted way out on the Internet, to no avail.
If you surf the Internet on a computer instead, Hidden24 provides good protection.
Read More
- Wikipedia on Pegasus: https://en.wikipedia.org/wiki/Pegasus_(spyware)
- A very accurate technical description of how Pegasus works: https://info.lookout.com/rs/051-ESQ-475/images/pegasus-exploits-technical-details.pdf
- “HIDE AND SEEK Tracking NSO Group’s Pegasus Spyware to Operations in 45 Countries” An excellent compilation by four researchers at the University of Toronto’s Citizen Lab, showing all the different Pegasus operators, where they are, their purposes and the countries and areas they monitor, as well as the methods used to detect the operators. The researchers also report their communication with NSO, which of course has no idea at all about what the researchers are talking about. Download the PDF from Researchgate: https://www.researchgate.net/publication/327752350_HIDE_AND_SEEK_Tracking_NSO_Group’s_Pegasus_Spyware_to_Operations_in_45_Countries
- Amnesty International too, has investigated how Pegasus spreads, suspicious addresses on the Internet, easily infected Apple apps, how Pegausus tries to hide in the phone and how it sometimes fails. In section 9.5 there is a list of servers that Pegasus communicates with, which are used to redirect your browser to a malicious site, which you can investigate. But remember that these addresses are constantly changing and may no longer be relevant. You will find China, as well as California and Iceland. This survey is, more or less, up-to-date for the year 2021: https://www.amnesty.org/en/latest/research/2021/07/forensic-methodology-report-how-to-catch-nso-groups-pegasus/
- Search page where you can find the vulnerable people on the Pegasus list: https://cdn.occrp.org/projects/project-p/#/
- Yet another news item: https://www.theallineed.com/technology/20210719/pegasus-50000-people-hacked-including-many-journalists-and-opponents/
- All technical questions and answers can be found here: https://www.lookout.com/search#q=pegasus+exploits
-
By Jörgen Städje, Hidden24
MORE ARTICLES TO READ

VPN
Fredrik added temp title
<a href=”https://www.hidden24.co.uk/wp-content/uploads/2021/09/Pegaz_Opera_Poz...

Internet Security
Top 19 tips for cyber security in business
IT security concern in everyone in the company. From office workers and up to company m...

VPN
Top 10.0 tips for cyber security in business
IT security concern in everyone in the company. From office workers and up to company m...

VPN
Top 5 tips for cyber security in business and its
Top 5 tips for cyber security in business IT security concern in everyone in the compan...

VPN
Top 10 tips for cyber security in business
Top 5 tips for cyber security in business IT security concern in everyone in the compan...

Uncategorized
Privacy Spotlight: How to keep your android safe from hackers
Protecting your android from hackers goes a long way to maintaining your privacy online...

Uncategorized
VPN: The Ultimate Beginners Guide
VPNs are quite popular with everyone in today’s world. VPNs are not a new concept by an...